5 Strategies for Effective Identity Security Breach Management
Authentication and authorization systems that prioritize…
Innovative technology transforming how we learn and lead.

Authentication and authorization systems that prioritize…
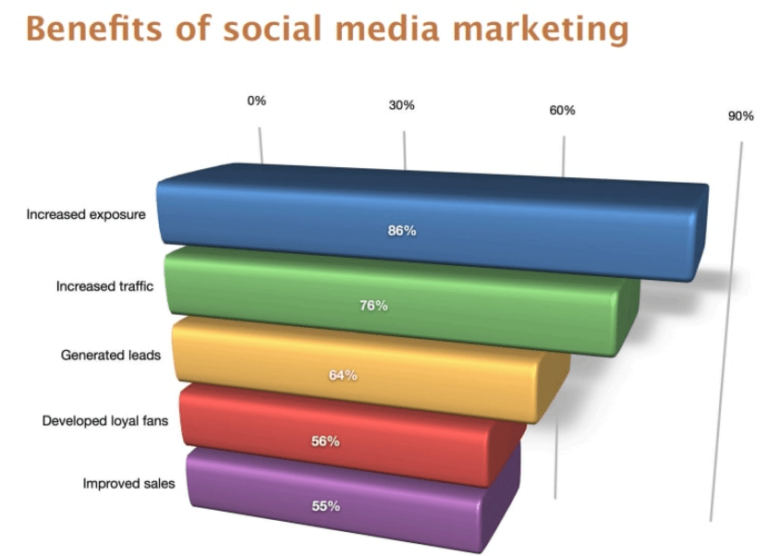
Are you looking for the best…

A recent study from the Massachusetts…

Years back, we had to travel…

The synergy between science and technology…

New CNC machining project development concept…

In the modern business landscape, efficiency…

For too long, the education system…

Prepaid cell phones offer a range…

In the ever-evolving realm of technology,…